The default security configuration for Fedora Core protects your system without restricting any of the functions of a desktop or laptop computer. If you are installing a server, you may need to alter these settings so others can access the system.
Select Next to proceed after you review the security configuration and make any necessary changes.
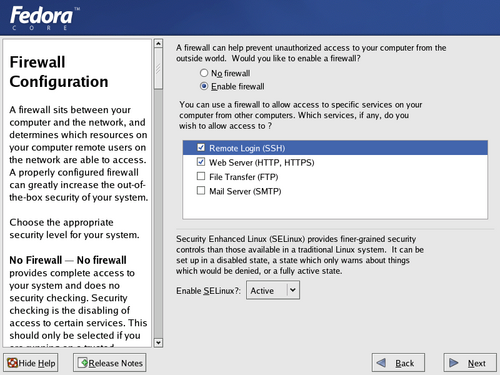
The firewall built into Fedora Core checks every incoming and outgoing network connection on your machine against a set of rules. These rules specify which types of connections are permitted and which are denied.
By default the firewall is enabled, with a simple set of rules that allow connections to be made from your system to others, but block incoming connections from other systems. By making changes on this screen, you can allow access to specific network services on your Fedora system.
To enable access to services listed on this screen, click the checkbox next to the service name. After installation is complete, you can enable access to other services as well.
Avoid disabling the firewall. If you believe it is necessary to do so, however, select No firewall.
![[Tip]](./stylesheet-images/tip.png) | Changing the firewall settings |
|---|---|
To change these settings later, use the system-config-securitylevel utility. From the main menu, choose Desktop->System Settings->Security Level and Firewall. | |